
Introduction:
In the era of digitalization, where technology constantly reshapes the way, we live and work, cybersecurity has become an increasingly crucial aspect of our daily lives. Ride-sharing giant Uber, known for revolutionizing transportation services, found itself at the epicenter of a cybersecurity storm when it fell victim to a significant cyber attack. This blog is about Uber cyber attack, exploring its impact on the company, its users, and the broader landscape of cybersecurity.
The Uber Cyber Attack Unveiled:
The cyber-attack on Uber occurred in 2016, revealing the vulnerability of even the most tech-savvy corporations. The breach involved the unauthorized access of personal information belonging to millions of Uber users and drivers. Hackers exploited a weakness in Uber’s security infrastructure, gaining access to a treasure trove of sensitive data.
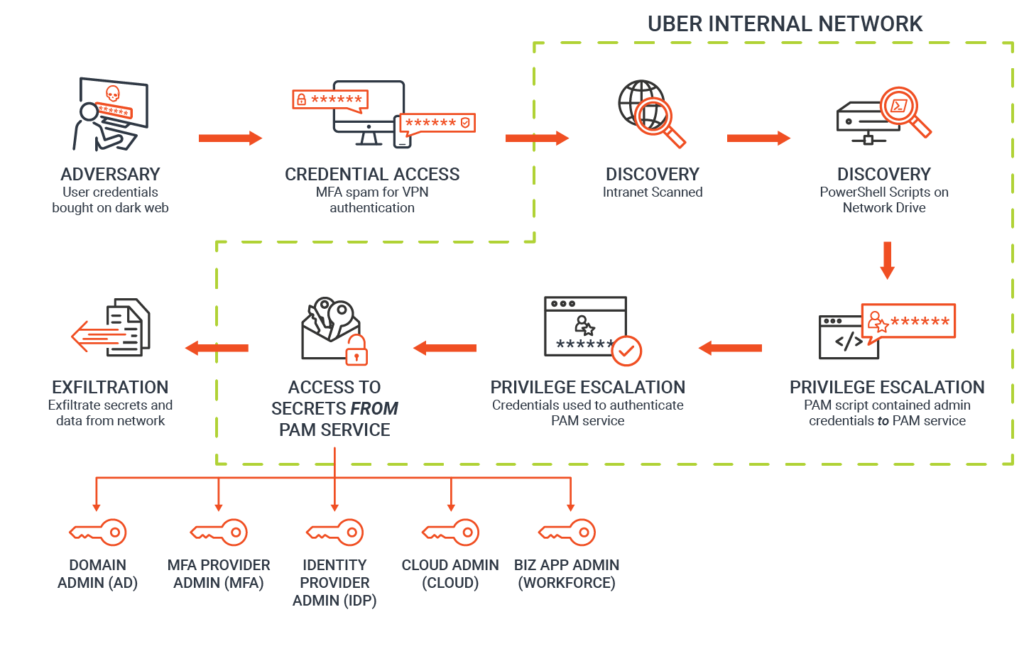
Timeline of the 2016 Uber Cyber Attack:
1. October 2016: The Cyber Attack Occurs
- Hackers breach Uber’s systems and gain unauthorized access to the personal data of over 57 million Uber users and 600,000 drivers worldwide. The stolen data includes names, email addresses, phone numbers, and in the case of US drivers, approximately 600,000 driver’s license numbers.
2. November 2016: Discovery of the Breach
- Uber becomes aware of the cyber attack on its systems.
3. Late 2016 – Early 2017: Uber Pays Hackers
- Instead of disclosing the breach to the public or notifying affected individuals, Uber decides to pay the hackers $100,000 to delete the stolen data and keep the breach quiet. This decision to conceal the breach and pay off the hackers would later draw significant criticism.
4. November 2017: Uber Discloses the Breach
- More than a year after the cyber attack occurred, Uber finally discloses the breach to the public. The delayed disclosure raises concerns and leads to widespread criticism of Uber’s handling of the incident.
5. December 2017: Fallout and Executive Resignations
- In the aftermath of the disclosure, Uber faces significant backlash from regulators, users, and privacy advocates. Several executives, including the Chief Security Officer, resign from their positions. Travis Kalanick, the CEO at the time, steps down amid mounting controversies surrounding Uber’s corporate culture and management practices
6. Regulatory Scrutiny and Legal Challenges
- Uber faces regulatory scrutiny and legal challenges from various US states and regulatory bodies, including the Federal Trade Commission (FTC). The company is compelled to settle with regulators and pay fines for its mishandling of the cyber attack and failure to promptly disclose the breach.
7. Repercussions and Remediation Efforts
- In the wake of the breach, Uber implements measures to enhance its cybersecurity defenses and improve data protection practices. The company undergoes internal restructuring and appoints new leadership to rebuild trust and address systemic issues within the organization.
The Stolen Data:
During the 2016 Uber cyberattack, much personal data was exposed, affecting platform users and drivers. The leaked data contains personal information for over 57 million Uber users globally.
This information usually includes:
- Names
- Email addresses
- Phone numbers
- Driver information.
Around 600,000 Uber drivers’ data was exposed, mostly in the US. The data may have included names, email addresses, phone numbers, driver’s licence numbers, and payment information. While Uber claims that financial information such as credit card numbers and bank account information were not hacked, the breach did reveal vast amounts of personally identifiable information (PII) that might be used for fraudulent activity or identity theft.
Other Data: Other types of information may have been compromised during the incident, though specifics beyond user and driver data have yet to be officially published. However, the types of data commonly stored by a corporation like Uber, such as trip records and location data, may have also been at danger.
The exposure of such sensitive data has created major privacy, security, and trust concerns among Uber customers and drivers. It also emphasised the importance of organisations implementing strong cybersecurity measures to secure customer information from unauthorised access and reduce the possibility of data breaches.
Immediate Fallout:
The fallout from the cyber-attack was swift and impactful. Uber, a company that prided itself on its commitment to user safety, faced severe backlash as users and drivers alike grappled with the potential consequences of having their personal information exposed. Trust in the platform was shattered, and the incident highlighted the need for robust cybersecurity measures in the tech industry.
Uber’s Response:
In the wake of the cyber attack, Uber faced a dual challenge of the immediate damage and restoring the trust of its user base. The company promptly disclosed the breach to the public, acknowledging the scale of the incident and the potential risks posed to affected individuals. Uber also took immediate steps to enhance its cybersecurity infrastructure and collaborated with law enforcement agencies to track down the perpetrators.
Legal Consequences:
The Uber cyber attack did not only tarnish the company’s reputation but also brought about legal consequences.
Regulatory bodies and authorities imposed hefty fines on Uber for its failure to safeguard user data adequately. The incident prompted a broader conversation about the accountability of tech companies in ensuring the security and privacy of user information.
Lessons Learned:
Several important lessons can be gained from the Uber cyber attack.
- Openness Is Key: Uber’s delayed notification of the breach negatively impacted the company’s image and weakened customer confidence. When it comes to cybersecurity issues, it’s crucial to be transparent so that those affected and those who need to know may take the appropriate steps to reduce risks.
- Make Data Security a Top Priority: The incident drove home how critical it is to keep private information secure. Protecting user information from unauthorised access requires companies to use strong encryption mechanisms, access controls, and data security processes.
- Proactive Cybersecurity Measures: Since cyber threats are ever-changing, organisations need to take proactive steps to protect themselves from cyber attacks. Among these measures are cybersecurity awareness training programmes, threat intelligence collecting, and regular security audits.
- Concerns about Uber’s adherence to data protection standards including the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) surfaced in its aftermath. To avoid heavy fines and legal consequences, businesses must make sure they are following all applicable rules and laws.
What could have been done to prevent the breach:
Although complete prevention is difficult to ensure, there were a number of steps that might have been taken to lessen the likelihood of the 2016 Uber cyberattack:
- Strong Cybersecurity Infrastructure: Protecting against unauthorised access to sensitive data can be achieved by putting in place a strong cybersecurity infrastructure that includes firewalls, intrusion detection systems, and encryption techniques.
- Regular Security Audits and Vulnerability Assessments: By carrying out regular security audits and vulnerability assessments, it is possible to find system vulnerabilities that hackers might exploit. Through quick remediation of these vulnerabilities, organisations can lower the probability of a successful breach.
- Employee Training and Awareness: Putting money into thorough cybersecurity training programmes for staff members can help reduce the risk of phishing and insider threats by educating them about cybersecurity best practices. Workers should receive training on identifying and successfully handling any security risks.
- Multi-factor authentication (MFA): Adding an extra layer of security to sensitive systems and data access through the use of MFA makes it hard for unauthorised users to obtain access, even with stolen credentials.
- Data Encryption and Access Controls: In the event of a breach, the exposure of private information can be minimised by encrypting sensitive data and putting strict access controls in place. Sensitive data should only be accessed by authorised individuals, and encryption should be used both while the data is in transit and when it is at rest.
- Timely Patch Management: You can help fix known vulnerabilities and stop cyber attackers from exploiting them by making sure that software and systems are updated with the newest security patches on a regular basis.
- Incident Response Plan: It is imperative to have a thorough incident response plan that details procedures for identifying, handling, and recovering from cybersecurity issues. In the case of a breach, this strategy should outline how affected parties and pertinent authorities would be notified quickly.
- Third-Party Risk Management: It’s critical to evaluate and keep an eye on the security procedures used by outside contractors and service providers who have access to private information. To reduce the danger of supply chain attacks, organizations should make sure that their partners follow strict cybersecurity standards and procedures.
- Frequent Security Drills and Training: Regular cybersecurity training and simulated breach exercises can assist stakeholders and staff become better equipped to handle possible security events. By being proactive, you can reduce the effect of a breach and speed up event response times.
- Developing a Culture of Security: An organization’s ability to withstand cyberattacks can be greatly increased by cultivating a culture of security where cybersecurity is given top priority at all levels. Workers ought to be aware of their responsibility for upholding cybersecurity and should be urged to report any questionable activity right away.
Although total protection from cyberattacks cannot be guaranteed, a company’s cybersecurity posture can be strengthened, and the danger of a breach can be greatly decreased by combining these preventive steps. A strong cybersecurity plan must include proactive risk management, constant awareness, and a dedication to continuous development.
Conclusion:
The Uber cyber-attack stands as a cautionary tale in the realm of cybersecurity. It illuminates the vulnerability of even the most prominent tech entities and emphasizes the importance of staying ahead in the perpetual cat-and- mouse game with cyber threats.
To reduce the risk of such cyber-attacks, all organizations must prioritize cyber security training to their employees to impart knowledge and ensure they operate with a security aware mindset. To master in-demand key cyber skills individuals can join T-CCBP (The Hacker Central Certified Cyber Blue Professional) certification course by The Hacker Central
As we navigate an increasingly interconnected digital world, the lessons learned from incidents like these must guide us toward a future where data security is paramount.