
Introduction:
In the ever-evolving landscape of cybersecurity, the importance of hands-on experience cannot be overstated. As the digital realm becomes increasingly complex and threats grow in sophistication, theoretical knowledge alone is no longer sufficient to combat cyber threats effectively. Hands-on experience plays a pivotal role in preparing cybersecurity professionals to navigate the intricate challenges of securing digital assets, identifying vulnerabilities, and developing robust defence mechanisms. This article explores the significance of hands-on experience in cybersecurity, examining how practical engagement enhances skills, fosters critical thinking, and ultimately strengthens the cybersecurity workforce.
Real-world Application of Knowledge:
One of the primary advantages of hands-on experience in cybersecurity is the translation of theoretical knowledge into practical skills. While classroom learning provides a foundation of concepts and theories, real-world scenarios often differ significantly from textbook examples. Hands-on experience enables cybersecurity professionals to bridge the gap between theory and application, allowing them to understand how to implement security measures in actual environments. Engaging with hands-on exercises, simulations, and practical labs provides an opportunity to apply theoretical concepts to realistic situations.
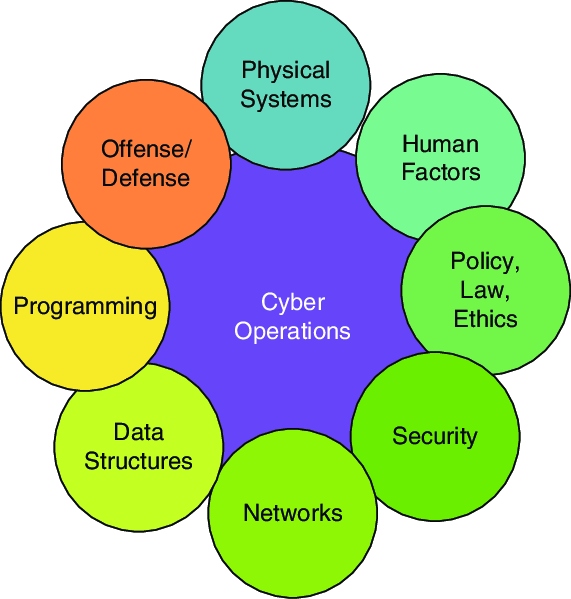
Building Practical Skills:
Cybersecurity is not a realm where bookish knowledge alone can provide a robust defence against cyber threats. Hands-on experience is the key to building practical skills that allow professionals to understand the nuances of real-world scenarios. Theoretical knowledge provides a foundation, but it is the application of that knowledge in hands-on exercises that solidifies understanding.
In hands-on labs, cybersecurity practitioners simulate various cyber-attacks, test security controls, and develop and implement defence strategies. These exercises go beyond textbook scenarios, allowing individuals to encounter the unpredictable nature of cyber threats. This practical exposure helps in developing a comprehensive skill set, including proficiency in penetration testing, vulnerability assessment, and network defence.
Building Practical Skills:
Cybersecurity is not a realm where bookish knowledge alone can provide a robust defence against cyber threats. Hands-on experience is the key to building practical skills that allow professionals to understand the nuances of real-world scenarios. Theoretical knowledge provides a foundation, but it is the application of that knowledge in hands-on exercises that solidifies understanding.
In hands-on labs, cybersecurity practitioners simulate various cyber-attacks, test security controls, and develop and implement defence strategies. These exercises go beyond textbook scenarios, allowing individuals to encounter the unpredictable nature of cyber threats. This practical exposure helps in developing a comprehensive skill set, including proficiency in penetration testing, vulnerability assessment, and network defence.
Exposure to Diverse Technologies and Tools:
The cybersecurity ecosystem comprises a vast array of technologies, tools, and frameworks. Hands-on experience provides individuals with exposure to this diversity, allowing them to become proficient in using the tools that are instrumental in securing digital assets.
Through practical exercises and labs, cybersecurity professionals gain familiarity with firewalls, intrusion detection systems, encryption tools, and various cybersecurity frameworks. This exposure is instrumental in preparing them for the multifaceted challenges they may encounter in their roles, ensuring a well-rounded skill set that covers different aspects of cybersecurity.
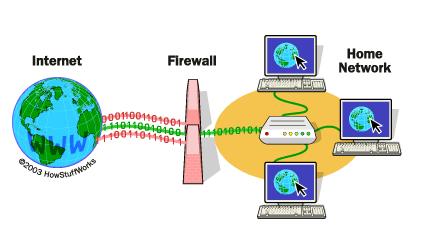
1. Firewalls:
Firewalls act as a barrier between a secure internal network and external networks, such as the internet. They control and monitor incoming and outgoing network traffic based on predetermined security rules. Firewalls play a crucial role in preventing unauthorized access and protecting against various cyber threats by filtering and blocking potentially harmful data.
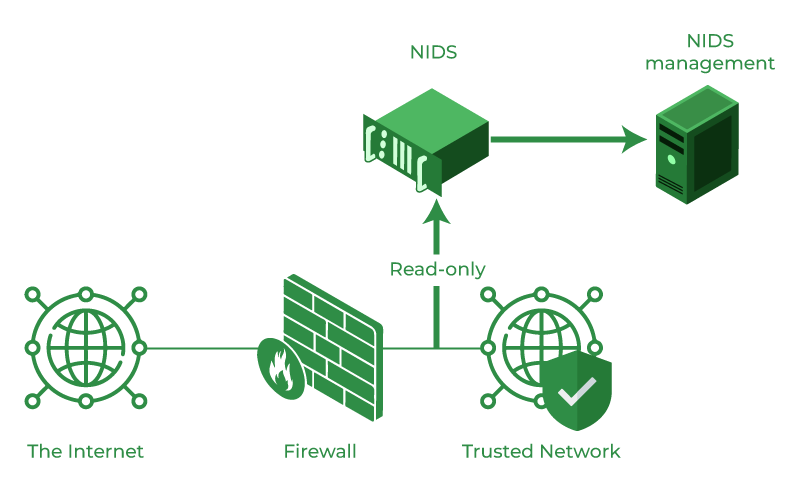
2. Intrusion Detection Systems (IDS):
IDS monitors network or system activities for suspicious patterns or behaviours that may indicate a security threat. It can be classified into two types: network-based (NIDS) and host-based (HIDS). NIDS analyses network traffic, while HIDS monitors activities on individual devices. IDS alerts administrators to potential security incidents, helping them respond promptly to mitigate risks.
3. Encryption Tools:
Encryption tools secure sensitive data by converting it into a coded format that can only be deciphered with the appropriate key. This technology ensures confidentiality and privacy, protecting information from unauthorized access or interception. Common encryption tools include Secure Sockets Layer (SSL) for web communications and Pretty Good Privacy (PGP) for email encryption.
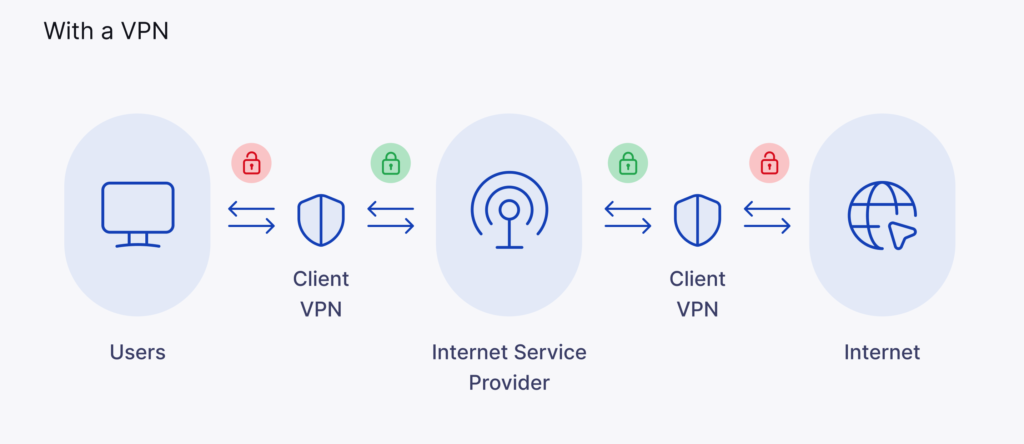
4. Virtual Private Networks (VPNs):
VPNs create secure, encrypted connections over the internet, allowing users to access a private network remotely. This technology is crucial for ensuring the confidentiality and integrity of data transmitted between a user and the network. VPNs are widely used to establish secure connections for remote workers, providing a secure tunnel for data transmission.
5. Security Information and Event Management (SIEM) Systems:
SIEM systems collect and analyse log data from various sources across an organization’s IT infrastructure. By correlating and analysing this data, SIEM systems can detect and respond to security incidents. SIEM tools provide a centralized platform for monitoring and managing security events, helping organizations gain insights into potential threats and vulnerabilities.
6. Penetration Testing Tools:
Penetration testing tools simulate cyber-attacks to identify and exploit vulnerabilities in a system or network. Ethical hackers use these tools to assess the security posture of an organization and provide insights into potential weaknesses. Examples of penetration testing tools include Metasploit, Burp Suite, and Nmap, which help security professionals assess and strengthen defences.
7. Endpoint Protection Software:
Endpoint protection software safeguards individual devices (endpoints) within a network from various cyber threats. These threats may include malware, ransomware, and other malicious activities. Endpoint protection tools often include antivirus, anti-malware, and firewall features, providing a comprehensive defence against threats that could compromise the security of individual devices.
8. Security Orchestration, Automation, and Response (SOAR) Platforms:
SOAR platforms integrate and automate security processes, enhancing the efficiency of incident response and threat detection. These platforms enable organizations to orchestrate workflows, automate repetitive tasks, and respond rapidly to security incidents. SOAR tools help streamline security operations, reducing response times and minimizing the impact of cyber threats.
9. Security Assessment and Vulnerability Scanning Tools:
Security assessment tools identify and assess vulnerabilities within a system or network. These tools conduct automated scans to discover potential weaknesses that could be exploited by attackers. Vulnerability scanning tools, such as Nessus and OpenVAS, help organizations proactively identify and address security vulnerabilities before they can be exploited.
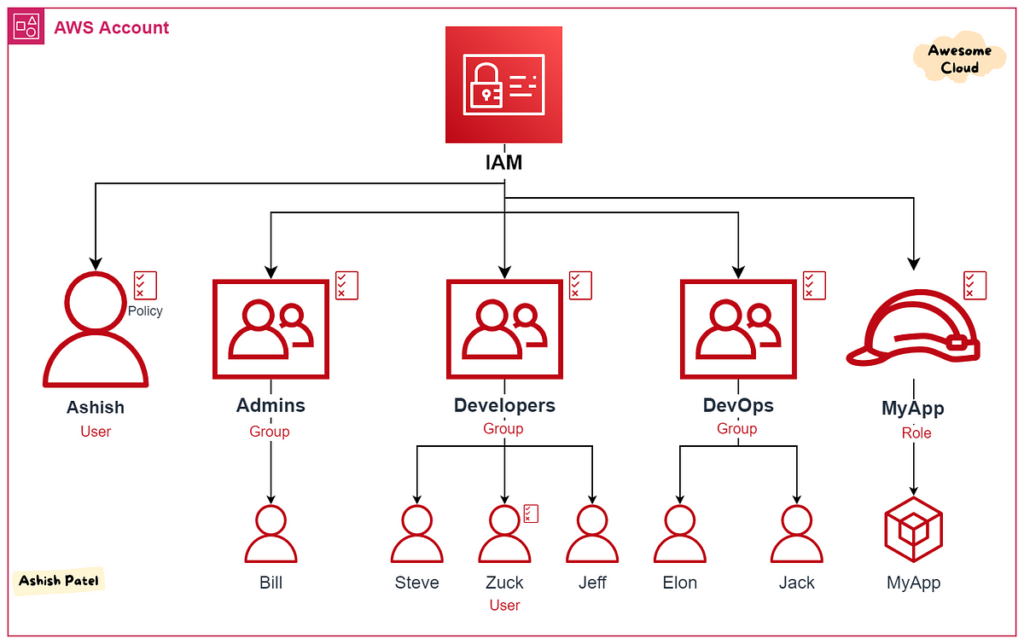
10. Identity and Access Management (IAM) Solutions:
IAM solutions manage and control user access to IT resources, ensuring that only authorized individuals can access specific systems or data. These solutions encompass authentication, authorization, and user management processes. IAM tools help organizations enforce security policies, mitigate the risk of unauthorized access, and maintain control over user privileges within the network.
Immersive Learning Environments:
Hands-on experience is often gained through immersive learning environments such as virtual labs and cyber ranges. These environments replicate the complexities of actual systems and networks, providing a safe space for individuals to experiment with different tools and techniques.
By engaging in simulated environments, individuals can practice identifying and mitigating vulnerabilities, responding to incidents, and fine-tuning their analytical and problem-solving skills. This hands-on approach helps bridge the gap between theoretical knowledge and practical application, fostering a deeper understanding of cybersecurity concepts.
Real-world Incident Response:
One of the critical aspects of cybersecurity is incident response. When a security incident occurs, the ability to respond swiftly and effectively can make the difference between minimal impact and catastrophic consequences. Hands-on experience prepares cybersecurity professionals for real-world incident response by exposing them to simulated attacks and breaches.
Through hands-on exercises, individuals learn how to detect and analyse security incidents, contain and mitigate the impact, and implement measures to prevent future occurrences. This practical experience is invaluable in honing the skills needed to handle the dynamic and unpredictable nature of cyber threats.
Developing a Cybersecurity Mindset:
Hands-on experience not only imparts technical skills but also fosters a cybersecurity mindset. This mindset involves thinking like a hacker to anticipate and understand potential vulnerabilities. By actively engaging in simulated attacks, cybersecurity professionals gain insights into the tactics, techniques, and procedures employed by malicious actors.
Understanding the mindset of cyber adversaries is crucial for developing effective defence strategies. Hands-on experience allows individuals to think critically, analyse situations from an attacker’s perspective, and proactively strengthen security measures to stay one step ahead of potential threats.
Career Advancement and Specialization:
Hands-on experience plays a pivotal role in career advancement within the cybersecurity field. As professionals gain practical skills, they become better equipped to take on more complex roles and responsibilities. Employers increasingly value hands-on experience when making hiring decisions, as it demonstrates an individual’s ability to navigate the challenges of the cybersecurity landscape.
Moreover, hands-on experience allows cybersecurity professionals to specialize in specific domains such as penetration testing, incident response, or threat intelligence. Specialization is becoming increasingly important in the cybersecurity job market, and hands-on experience is the foundation upon which these specialized skills are built.
Industry Collaboration and Networking:
Engaging in hands-on experiences often involves collaboration with peers, mentors, and industry experts. This collaborative environment not only facilitates knowledge sharing but also provides opportunities for networking within the cybersecurity community. Networking is crucial for staying updated on the latest trends, sharing insights, and accessing potential career opportunities.
Participating in hands-on workshops, conferences, and cybersecurity competitions allows individuals to connect with like-minded professionals, share experiences, and gain insights from others in the field. These connections can prove instrumental in career growth, knowledge acquisition, and staying abreast of emerging threats and technologies.
Addressing the Cybersecurity Skills Gap:
The cybersecurity industry is facing a significant skills gap, with a shortage of qualified professionals to meet the increasing demand for cybersecurity expertise. Hands-on experience serves as a practical solution to address this gap by preparing individuals for real-world challenges. By actively engaging in simulated environments, aspiring cybersecurity professionals can bridge the divide between academic knowledge and the practical skills demanded by the industry.
Conclusion:
In conclusion, the significance of hands-on experience in cybersecurity cannot be overstated. As the digital landscape evolves, the demand for skilled professionals capable of navigating complex cyber threats continues to rise. Gaining the edge in this dynamic field requires more than theoretical knowledge; it demands practical proficiency honed through hands-on experiences. This hands-on approach fosters adaptability, problem-solving abilities, and a heightened sense of awareness crucial for effective cyber defence. Employers increasingly prioritize candidates with practical experience, recognizing that it is the key to staying ahead of sophisticated cyber adversaries. In a realm where the stakes are high and threats constantly evolve, hands-on experience emerges as the linchpin for success, empowering cybersecurity professionals to proactively safeguard digital assets and contribute to the resilience of the digital ecosystem.