
Introduction:
In an era dominated by smartphones and tablets, our lives are intricately woven into the fabric of mobile technology. From personal conversations to financial transactions, our mobile devices play a pivotal role in nearly every aspect of our daily lives. With this increased reliance on mobile technology comes a pressing need for robust mobile device security.
In this blog post, we’ll delve into the essentials of mobile device security, exploring the threats, vulnerabilities, and best practices to fortify your digital fortress.
Why is Mobile Security important?
Mobile devices’ constant internet connectivity makes them an appealing target for cyber criminals, thus serving as an attractive attack vector.
Given the constant discovery of new vulnerabilities, it is crucial to remain vigilant and stay informed about any potentially suspicious activity occurring on your device.
Mobile devices can be attacked on multiple levels. Understanding the importance of cybersecurity and recognizing the most common threats and vulnerabilities is critical for protecting against mobile threats.
What are the signs your Mobile device is infected?
Malware infection on your mobile device could be indicated by several indicators.
They consist of:
Rapid battery depletion: Malware can frequently accelerate the rate at which a battery empties. If your device’s battery diminishes at an abnormally rapid rate, you should consider running a malware scan.
Slowdown: An additional indicator of malicious software is a gradual slowdown of the device. Malware could potentially cause longer application loading times or a general decrease in the device’s performance.
Abnormal behavior: Red flags include sudden changes in settings, programs that open and close unexpectedly, an excessive number of pop-ups, an increase in data usage, and the appearance of new and unfamiliar icons on the screen.
Upon the gradual detection of any of these indicators, it is crucial that you perform an urgent malware scan on your device. Following this, you should update any security applications and software on your device and alter any passwords that have been saved there.
Mobile devices require security measures the same as computers.
What measures may be taken to safeguard your phone and tablet from unauthorized access by hackers?
Please check our guide to mobile security below.
Mobile cyberthreats are frequently viewed by the public as all-encompassing threats. However, there are several kinds of mobile cyberthreats to be mindful of.
They include:
Application-based threats:
Application-based mobile threats encompass risks and vulnerabilities that specifically target mobile applications (apps), hence presenting security and privacy concerns for users. These risks involve a range of harmful actions, such as spreading malware-infected or counterfeit applications, taking advantage of insecure application permissions, intercepting application communications through man-in-the-middle attacks, and exploiting weaknesses in third-party libraries.
In addition, threats that originate from mobile applications might encompass many malicious activities such as phishing, social engineering, adware, data leakage, and privacy infringements. These activities can jeopardize the security of users’ sensitive information and the integrity of their devices.
To alleviate these hazards, users should show prudence while downloading applications, consistently update their applications and operating systems, and scrutinize app permissions prior to installation.
Developers must prioritize implementing secure coding techniques, regularly perform security assessments, and swiftly resolve any revealed vulnerabilities to bolster the security of their applications and safeguard users from attacks.
Web-based threats:
Occurs when you visit a website that appears normal on the surface but secretly downloads harmful content onto your device through its hidden components. Web-based risks encompass several forms of cyber attacks, such as phishing schemes and drive-by downloads.
Network-based threats:
These threats exploit weaknesses in wireless networks, cellular networks, and internet connections to compromise device security and intercept sensitive information.

Physical threats:
Physical threats occur when you lose or have your cell phone stolen. This is the most serious mobile threat since attackers can gain direct access to critical personal information saved on the phone.
Understanding the Threat:
Malware Threats: Mobile devices are not immune to the ever-present threat of malware. From malicious apps to phishing schemes, users must be attentive in protecting their devices against unwarranted intrusions.
Data Breach Dangers: The data stored on our mobile devices is a treasure trove for cybercriminals. Protecting personal information, sensitive documents, and login credentials is paramount to prevent data breaches.
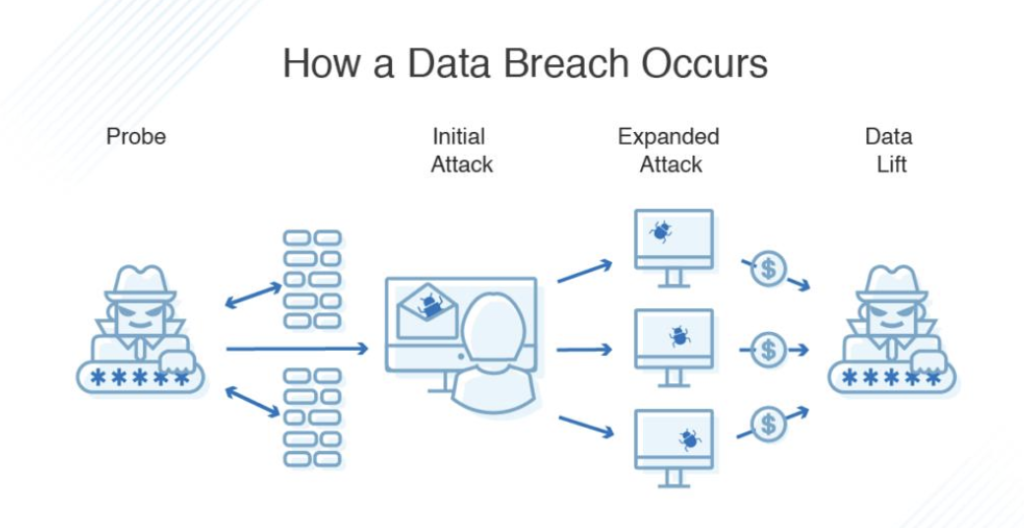
3. Unsecured Networks: Connecting to public Wi-Fi networks can expose your device to various security risks. Man-in-the-middle attacks and network eavesdropping are potential threats when using unsecured Wi-Fi.
4. Vulnerabilities in web browsers: Browser attacks leverage existing vulnerabilities in your mobile browser to exploit them. If you observe any alteration in the appearance of your mobile browser, it is possible that you have fallen victim to a browser exploit assault.
5. Jailbroken or Rooted Devices: Taking control of the administrator powers on iOS and Android smartphones is known as jailbreaking and rooting a device. These attacks rely on taking advantage of OS vulnerabilities and accessing data since rooting or jailbreaking provides more permissions. To have greater flexibility with their mobile devices, some users prefer that their devices be jailbroken or rooted.
Best Practices for Mobile Device Security:
- Device Encryption: Enable device encryption to safeguard your data in case your device falls into the wrong hands. This ensures that even if someone gains physical access to your device, they cannot easily access your data without the encryption key.

- Building a Support System:- Building a strong support system is essential for individuals balancing work and study commitments. Whether it involves seeking guidance from mentors, collaborating with peers in study groups, or enlisting the support of family and friends, having a network of individuals who understand and support one’s goals can provide invaluable encouragement and motivation.
- Engaging with Professional Associations:- Professional associations and organizations, such as the Information Systems Security Association (ISSA) or the International Association of Privacy Professionals (IAPP), offer networking opportunities, educational resources, and career development programs for cybersecurity professionals. By becoming actively involved in these associations, individuals can expand their professional network, stay informed about industry trends, and access valuable career resources and opportunities.
- Participating in Mentorship Programs:- Mentorship programs pair aspiring cybersecurity professionals with experienced mentors who can provide guidance, advice, and support as they navigate their career journey. By seeking mentorship from seasoned professionals in the field, individuals can benefit from their wisdom, insights, and expertise, gaining valuable perspective and direction on their path to success.
- Seeking help from online forums:- There are a plethora of online forums for nearly any topic you can think of. Leveraging the information shared in these forums can be extremely helpful to a cyber security student. It not only allows you to better understand the topic you’re studying, but also allows you to network and make friendships online.

Embracing Continuous Learning:
In the dynamic and rapidly evolving field of cybersecurity, continuous learning is not just a recommendation – it’s a necessity. As new threats emerge, technologies evolve, and best practices evolve, cybersecurity professionals must remain vigilant and proactive in their pursuit of knowledge and skill enhancement. Pursuing relevant certifications, such as T-SA, T-jPEN and T-CCBP, can bolster one’s credentials, validate expertise, and open doors to new career opportunities.
Staying Abreast of Industry Trends:
Staying informed about the latest trends, developments, and emerging technologies in cybersecurity is essential for professionals seeking to stay ahead of the curve. Whether it involves reading industry publications, attending webinars, or participating in online forums and communities, staying abreast of industry trends enables individuals to anticipate challenges, adapt to changes, and capitalize on new opportunities in the field.
Maintaining Work-Life Balance:
While the pursuit of professional advancement is commendable, it’s imperative not to overlook the importance of maintaining a healthy work-life balance. Burnout is a pervasive risk for individuals juggling the demands of full-time employment and academic pursuits, and neglecting self-care can have detrimental consequences on both physical and mental well-being. By prioritizing self-care, allocating time for relaxation, hobbies, and social activities, individuals can sustainably manage their workload and enhance their overall quality of life. While maintaining work-life balance sounds cliched and it may seem like it is not a priority, to be able to effectively learn complex cyber security topics for a longer duration requires an individual to be able to manage their stress levels well.
Conclusion:
Balancing a full-time job with studying for a career in cybersecurity is undeniably challenging, but it’s also a rewarding journey filled with opportunities for growth, development, and personal fulfillment. By adopting a strategic approach, leveraging resources, prioritizing tasks, seeking support, embracing continuous learning, and maintaining a healthy work-life balance, aspiring professionals can navigate this juggling act with confidence and success. Remember, the key lies in determination, perseverance, and a steadfast commitment to excellence in both professional and academic pursuits. With dedication and resilience, the goal of achieving a successful career in cybersecurity is well within reach.