
Introduction:
In the contemporary digital landscape, comprehending cyber threats is imperative for safeguarding information and systems. Cyber threats encompass a diverse range of malicious activities, from the infiltration of malware and phishing attacks to sophisticated hacking techniques. Understanding the various types of threats, vulnerabilities in software and hardware, and potential attack vectors is fundamental to devising robust cybersecurity strategies. As technology advances, so do the intricacies of cyber threats, necessitating continuous vigilance, proactive measures, and education. This introduction explores the multifaceted realm of cyber threats, emphasizing the importance of awareness, preparedness, and evolving security measures in our interconnected and digitally-driven world.
Where Do Cyber, Threats Come From?
Cyber threats can emanate from various sources, often driven by individuals, groups, or organizations with malicious intent. Understanding the origins of these threats is crucial for developing effective cybersecurity strategies. Here are some common sources of cyber threats:
Hackers and Cybercriminals:
Individuals: Skilled hackers or script kiddies (less experienced individuals) seeking financial gain, personal satisfaction, or simply causing disruption.
Organized Crime Groups: Sophisticated criminal organizations engaging in cyber activities for financial motives, such as identity theft, ransomware attacks, and data breaches.
Nation-State Actors:
Governments and their intelligence agencies may conduct cyber espionage, cyber warfare, or cyber terrorism to gain strategic advantages or disrupt adversaries.
Insiders:
Malicious insiders, including disgruntled employees, contractors, or business partners, who intentionally compromise security for personal gain or vendetta.
Hacktivists:
Activists or groups pursuing political or social goals may engage in cyber activities to promote their agenda, often defacing websites or disrupting services.
Script Kiddies:
Individuals with limited technical expertise who use pre-written scripts or tools to exploit vulnerabilities, typically for fun or to prove their skills.
Phishing and Social Engineering:
Cyber threats often exploit human vulnerabilities through phishing emails, social engineering tactics, or other deceptive methods to trick individuals into revealing sensitive information.
Cyber Espionage:
State-sponsored or corporate espionage involves the theft of sensitive information, intellectual property, or trade secrets to gain a competitive advantage.
Advanced Persistent Threats (APTs):
APTs are prolonged and targeted cyber-attacks orchestrated by well-funded and highly skilled adversaries, often with specific objectives such as infiltrating government systems or corporate networks.
Ransomware Developers:
Individuals or groups creating and distributing ransomware, which encrypts data and demands payment for its release. Ransomware attacks can be financially motivated.
Unsecured Internet of Things (IoT) Devices:
Insecure IoT devices can be exploited by cybercriminals to launch attacks. Compromised IoT devices may serve as entry points to larger networks.
Understanding the diverse sources of cyber threats highlights the need for a comprehensive and adaptive cybersecurity approach. This includes implementing security measures, staying informed about evolving threats, and fostering a cybersecurity-aware culture across individuals, organizations, and governments.

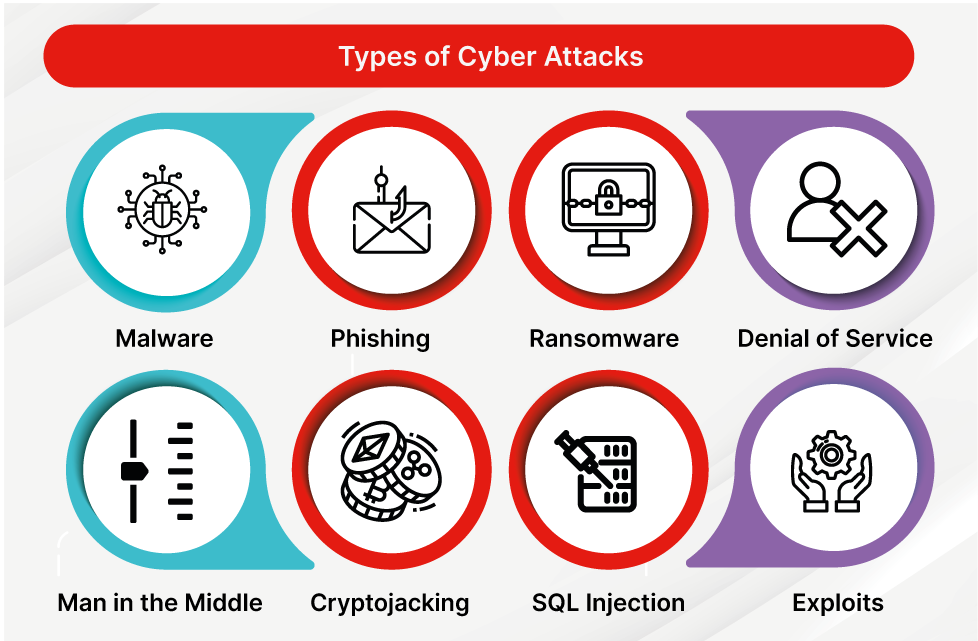
What are Examples of Cyber Threats?
Malware Attack:
A malware attack is a malicious infiltration of a computer system, encompassing various types of harmful software designed to compromise, damage, or exploit digital assets. Malware, an umbrella term for software such as viruses, trojans, worms, and ransomware, infiltrates systems through infected files, websites, or email attachments. Once inside, it can disrupt operations, steal sensitive information, or render files inaccessible. Ransomware, a prevalent form of malware, encrypts data, demanding a ransom for its release. Malicious actors continually refine their tactics, employing social engineering and advanced techniques to evade detection.
Phishing Attack:
Phishing attacks represent a pervasive and deceptive form of cyber threat, exploiting human vulnerability rather than technical weaknesses. In a typical phishing scenario, attackers craft fraudulent emails, messages, or websites, mimicking trusted entities to trick individuals into divulging sensitive information such as login credentials, financial details, or personal data. These deceptive communications often create a false sense of urgency or importance, urging recipients to click on malicious links or download infected attachments.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks:
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks are disruptive cyber threats aimed at overwhelming a target’s online services. In a DoS attack, a single source floods the target’s network, server, or website with traffic, rendering it inaccessible to legitimate users. DDoS attacks, on the other hand, involve multiple compromised devices, forming a botnet that orchestrates a synchronized assault. These attacks not only disrupt operations but also serve as a smokescreen for more insidious activities.
Man-in-the-Middle (MitM) Attacks:
Man-in-the-Middle (MitM) attacks involve cybercriminals intercepting and manipulating communication between two parties, surreptitiously gaining access to sensitive data. By exploiting vulnerabilities in networks or devices, attackers can eavesdrop on, alter, or redirect information, compromising the confidentiality and integrity of the data exchanged between users.
SQL Injection:
SQL Injection is a prevalent and malicious cyber-attack where hackers exploit vulnerabilities in a website’s database by injecting malicious SQL code. By manipulating user inputs, attackers can execute unauthorized database queries, potentially gaining access to sensitive information or even control over the entire database. This technique poses a significant threat to web applications that improperly handle user input, allowing cybercriminals to bypass security measures. Preventative measures, such as input validation and using parameterized queries, are crucial to thwart SQL Injection attacks and enhance overall cybersecurity in the ever-evolving digital landscape.
Zero-Day Exploits:
Zero-day exploits target undisclosed vulnerabilities in software, leveraging security flaws before developers can release patches or fixes. These attacks are particularly potent because defenders have zero days to prepare or defend against them. Cybercriminals or state-sponsored actors often exploit these undisclosed weaknesses, infiltrating systems, compromising data, and evading traditional security measures.

Why is it Necessary to Protect Against Cyber Threats?
Protecting against cyber threats is imperative due to the pervasive and severe consequences that can result from successful cyber-attacks. Here are key reasons highlighting the necessity of cybersecurity:
- Data Breach Prevention: Cyber threats often target sensitive data, including personal information, financial records, and intellectual property. Protecting against breaches is crucial to prevent unauthorized access, theft, or manipulation of valuable data.
- Financial Loss Mitigation: Cyber-attacks can lead to significant financial losses, including costs associated with remediation, legal repercussions, and potential damage to an organization’s reputation. Implementing robust cybersecurity measures helps mitigate these financial risks.
- Preservation of Reputation: A successful cyber-attack can tarnish an individual’s or organization’s reputation. Customers, clients, and partners may lose trust if confidential information is compromised. Cybersecurity safeguards help maintain trust and credibility in the digital age.
- National Security Concerns: Cyber threats are not limited to individuals or organizations; they also pose risks to national security. Protecting critical infrastructure, government systems, and defence networks is essential to safeguard a nation’s interests.
- Prevention of Service Disruptions: Cyber-attacks, such as DDoS attacks, can disrupt services, causing downtime for businesses or even affecting essential services like healthcare, energy, and transportation. Cybersecurity measures ensure the availability and continuity of services.
- Intellectual Property Protection: Many businesses and individuals rely on intellectual property for competitive advantage. Cybersecurity safeguards are essential to protect patents, trade secrets, and proprietary information from theft or unauthorized access.
- Compliance with Regulations: Various industries are subject to stringent data protection and privacy regulations. Adhering to these regulations is not only legally mandated but also crucial for maintaining the trust of customers and avoiding penalties.
- Prevention of Identity Theft: Cyber threats, such as phishing and identity theft, target individuals’ personal information. Protecting against these threats is vital to prevent financial losses, unauthorized access, and the misuse of personal data.
- Cyber Espionage Prevention: Nation-states and corporate entities engage in cyber espionage to gain a competitive advantage or extract sensitive information. Robust cybersecurity measures are essential to thwart such activities and protect national interests.
- Global Interconnectedness: In an era of global interconnectivity, cyber threats can have widespread and cascading effects. Protecting against these threats is essential to maintain stability in the interconnected digital ecosystem.
How to Protect Against and Identify Cyber Threats?
Protecting against and identifying cyber threats requires a multi-faceted approach that combines technological solutions, employee awareness, and proactive monitoring. Here are key strategies to enhance cybersecurity:
- Use Robust Antivirus and Anti-Malware Software: Deploy and regularly update antivirus and anti-malware solutions to detect and remove malicious software.
- Keep Software and Systems Updated: Regularly update operating systems, software, and applications to patch vulnerabilities and protect against known exploits.
- Implement Firewalls and Intrusion Detection Systems: Utilize firewalls and intrusion detection systems to monitor and filter network traffic, blocking unauthorized access and malicious activities.
- Secure Networks with Encryption: Encrypt sensitive data during transmission and storage to prevent unauthorized access, especially when using public networks.
- User Authentication and Access Controls: Enforce strong user authentication methods and restrict access privileges to minimize the risk of unauthorized access.
- Employee Training and Awareness: Conduct regular cybersecurity awareness training for employees to recognize and avoid phishing attacks, social engineering, and other common cyber threats.
- Implement Email Security Measures: Use email filtering and authentication mechanisms to block malicious emails and prevent phishing attempts.
- Zero-Trust Security Model: Adopt a zero-trust approach, where no user or system is automatically trusted, requiring continuous verification of identity and authorization.
- Regular Security Audits and Assessments: Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses in systems and processes.
- Monitor Network Traffic: Implement network monitoring tools to detect unusual or suspicious activities that may indicate a cyber threat.
Conclusion:
In conclusion, the ever-evolving landscape of cyber threats demands unwavering vigilance and proactive measures. As technology advances, so do the tactics of malicious actors, underscoring the critical importance of robust cybersecurity practices. From malware and phishing to sophisticated zero-day exploits, the potential risks to individuals, organizations, and even nations are substantial. A holistic approach encompassing technological solutions, employee awareness, and continuous monitoring is essential. By prioritizing cybersecurity, we fortify our digital defences, safeguard sensitive information, and mitigate the far-reaching consequences of cyber threats in our interconnected world. Constant adaptation and collaboration remain paramount in this ongoing battle to secure the digital realm.
Reference:
- Cybersecurity & Infrastructure Security Agency (CISA): CISA
- National Institute of Standards and Technology (NIST) – Cybersecurity Framework:NIST