Introduction:
In today’s rapidly evolving digital landscape, the need for robust cybersecurity measures has never been more critical. As technology advances, so do the threats, making it imperative for organizations and individuals alike to stay ahead of potential breaches and attacks. In this exploration of cutting-edge innovations in cybersecurity technology, we delve into the latest developments reshaping the field. From AI-driven threat detection and mitigation blockchain-powered authentication systems, these innovations promise to revolutionize how we safeguard sensitive data and digital assets. Furthermore, the emergence of quantum-resistant encryption algorithms and the integration of machine learning in security operations signifies a shift toward proactive defence mechanisms. As cyber-attacks become increasingly sophisticated and pervasive, understanding and harnessing these advancements is paramount in ensuring the resilience and integrity of our interconnected digital ecosystem. Join us as we delve into the forefront of cyber security innovation, where technology meets the challenge of safeguarding against evolving threats.
Artificial Intelligence and Machine Learning:
AI and ML have not only revolutionized cyber security by enabling proactive threat detection and response but have also significantly transformed the dynamics of cyber warfare. These technologies provide security professionals with powerful tools to anticipate and mitigate emerging threats before they can wreak havoc on organizations’ digital assets. One of the key advantages of AI-powered systems is their ability to analyse vast amounts of data in real-time, a task that would be virtually impossible for human operators alone. By processing data at lightning speed, AI algorithms can uncover subtle patterns and anomalies that might indicate malicious activity, thus enabling security teams to swiftly intervene and neutralize potential threats.
Moreover, ML algorithms continuously learn from new data, evolving and improving their detection capabilities over time. This iterative learning process allows cyber security systems to adapt to the ever-changing tactics and techniques employed by cyber adversaries, staying one step ahead in the ongoing cat-and-mouse game of cyber warfare. Techniques such as anomaly detection leverage ML algorithms to identify deviations from normal behaviour within a network or system, flagging suspicious activities that might otherwise go unnoticed.
In essence, AI and ML have become indispensable tools in the cyber security arsenal, empowering organizations to defend against an increasingly sophisticated and relentless cyber threat landscape. By harnessing the power of these technologies, security professionals can augment their capabilities, automate repetitive tasks, and focus their efforts on strategic threat mitigation strategies. However, it is crucial to recognize that AI and ML are not silver bullets and must be complemented with human expertise and oversight to effectively combat cyber threats.
Zero Trust Architecture:
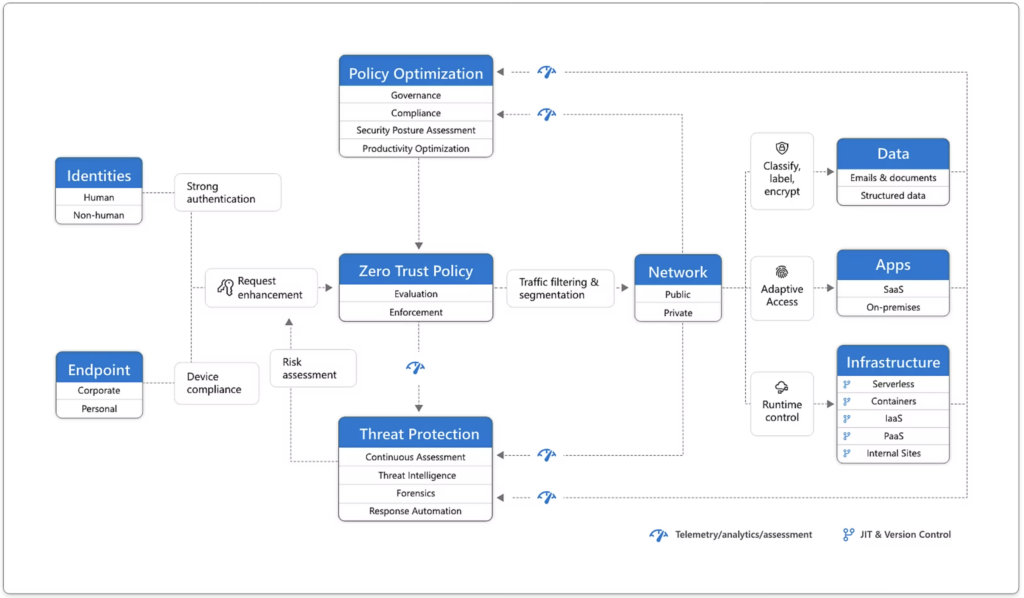
Zero Trust Architecture (ZTA) represents a paradigm shift in how organizations approach cybersecurity, rejecting the traditional perimeter-based model in favour of a more granular and dynamic approach to access control and network security. At its core, ZTA operates on the principle of “never trust, always verify,” assuming that threats could be both external and internal. Unlike traditional approaches that grant broad access to users within the network perimeter, ZTA adopts a model where access is granted on a least-privileged basis, regardless of whether the user is inside or outside the network.
Key components of ZTA include continuous authentication, micro-segmentation, and the principle of least privilege. These components work together to ensure that access is granted based on the specific context of the user, device, and application, thereby minimizing the attack surface and reducing the impact of potential breaches. Additionally, ZTA leverages technologies such as identity and access management (IAM), multifactor authentication (MFA), and encryption to enforce strict access controls and protect sensitive data. As organizations face increasingly sophisticated cyber threats, Zero Trust Architecture emerges as a proactive and adaptive approach to cybersecurity, providing enhanced protection against both external attacks and insider threats.
Quantum Cryptography:
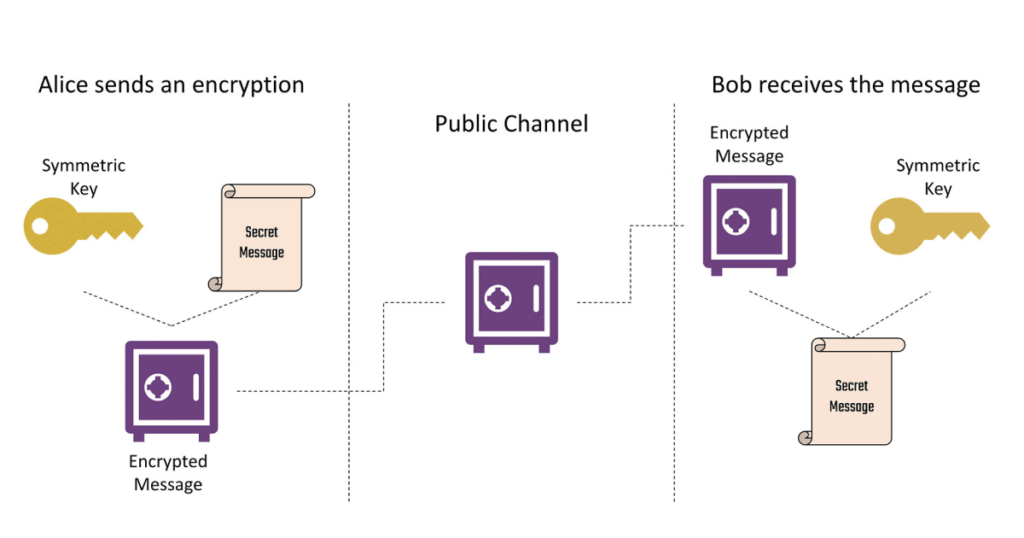
The advent of quantum computing poses a significant threat to traditional cryptographic algorithms, which form the foundation of modern cyber security. Quantum computers have the potential to break conventional encryption schemes, rendering sensitive data vulnerable to unauthorized access. In response, researchers have been exploring the field of quantum cryptography, which leverages the principles of quantum mechanics to develop secure communication protocols immune to quantum attacks. Technologies like quantum key distribution (QKD) enable the generation of cryptographic keys with provable security guarantees, offering a promising solution to the looming threat of quantum-enabled cyber-attacks.
In a typical QKD protocol, cryptographic keys are encoded into quantum states, such as the polarization of photons, and transmitted over a quantum channel. Any attempt to intercept these quantum states would inevitably disturb their delicate quantum properties, thus betraying the presence of an eavesdropper. Through techniques such as quantum entanglement and measurement, the legitimate parties can detect any tampering with the transmitted quantum states, ensuring the security of the key exchange process.
Secure Hardware:
Hardware-based security mechanisms play a crucial role in safeguarding sensitive information and protecting critical systems from tampering and exploitation. Trusted Platform Modules (TPMs), and Secure Enclaves (e.g., Intel SGX, ARM Trust Zone, and Hardware Security Modules (HSMs) provide a secure foundation for storing cryptographic keys, performing secure computations, and enforcing access control policies. Hardware Security Keys, such as USB tokens and smart cards, offer an additional layer of authentication for accessing digital assets and online services. By integrating secure hardware components into their infrastructure, organizations can enhance the resilience of their cyber security defences against a wide range of threats.
Deception Technology:
Deception technology disrupts the traditional approach to cyber defence by flipping the script on attackers. Instead of solely focusing on detection and mitigation, deception platforms proactively lure adversaries into engaging with decoy assets, such as fake servers, documents, and credentials. By planting breadcrumbs throughout the network, organizations can deceive, detect, and derail cyber threats in real time. Deception techniques not only provide early warning signs of potential breaches but also gather valuable intelligence on adversary tactics and techniques. As a result, defenders gain a strategic advantage in the ongoing battle against cyber adversaries.
Biometric Authentication:
As passwords continue to pose inherent security risks due to weak credentials and credential reuse, biometric authentication has emerged as a more secure alternative for verifying user identity. Biometric modalities, such as fingerprint recognition, facial recognition, iris scanning, and voice recognition, offer unique identifiers that are inherently tied to individual users. By leveraging biometric authentication, organizations can strengthen access controls, mitigate the risk of credential theft, and enhance the overall user experience. However, it is crucial to address privacy concerns and ensure the ethical use of biometric data to maintain user trust and compliance with regulatory requirements.
Blockchain Security:
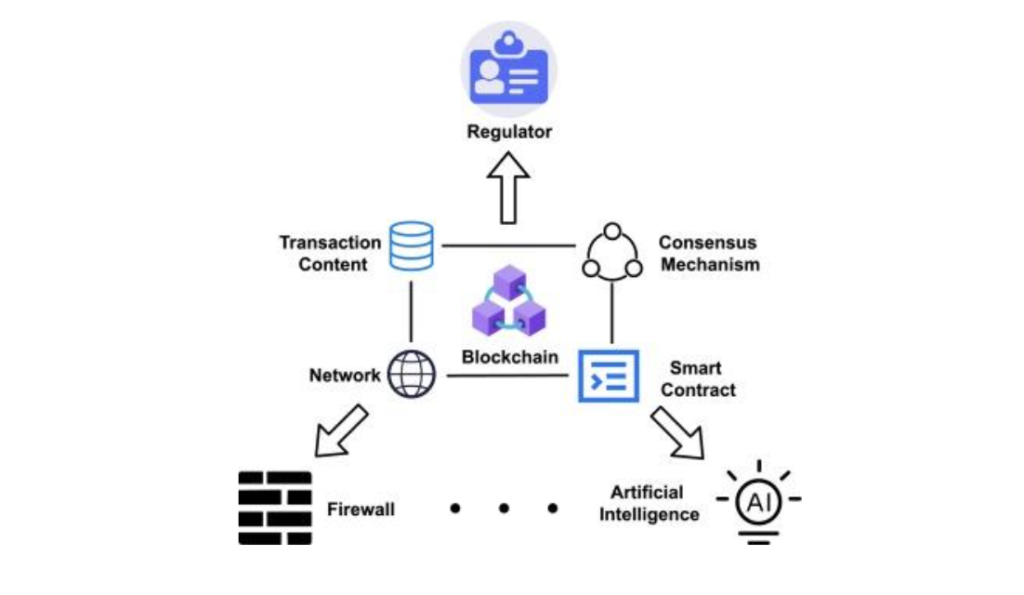
Originally devised as the underlying technology for cryptocurrencies like Bitcoin, blockchain has garnered significant attention for its potential applications beyond the realm of finance. In the context of cyber security, blockchain technology holds promise for enhancing data integrity, establishing secure identity management systems, and enabling tamper-resistant audit trails. By leveraging the decentralized and immutable nature of blockchain ledgers, organizations can mitigate the risk of data tampering, streamline the verification of transactions, and foster trust in digital interactions. Additionally, blockchain-based smart contracts offer a novel approach to automating and enforcing security policies in a transparent and tamper-evident manner.
Threat Intelligence Platforms
In the fight against cyber threats, knowledge is power. Threat Intelligence Platforms (TIPs) aggregate, analyse, and disseminate actionable threat intelligence to empower organisations in their cyber defence efforts. By monitoring various sources, such as open-source feeds, dark web forums, and security vendor reports, TIPs provide invaluable insights into emerging threats, adversary tactics, and indicators of compromise (IOCs). Through integration with security operations workflows, TIPs enable organisations to prioritise threats, orchestrate incident response actions, and continuously improve their security posture. Furthermore, the application of artificial intelligence and machine learning techniques enhances the efficacy of threat intelligence analysis, enabling proactive threat hunting and automated threat detection.
Endpoint Detection and Response (EDR)
Endpoints, including desktops, laptops, servers, and mobile devices, represent prime targets for cyber attackers seeking to infiltrate organizational networks. Endpoint Detection and Response (EDR) solutions offer real-time visibility into endpoint activities, allowing organizations to detect and respond to security incidents promptly. By monitoring endpoint telemetry, analysing behaviour patterns, and leveraging threat intelligence feeds, EDR solutions can identify malicious activities, contain threats, and remediate compromised endpoints effectively. Furthermore, the integration of EDR with other security controls, such as network detection and response (NDR) and security information and event management (SIEM) systems, enables holistic threat detection and response across the entire cyber security infrastructure.
Cyber Range Simulations
With cyber threats becoming increasingly sophisticated and diverse, organizations must continuously train and test their cyber security teams’ readiness to respond to cyber-attacks effectively. Cyber Range simulations provide a controlled environment for conducting immersive, scenario-based training exercises that replicate real-world cyber threats. By simulating cyber-attacks, defenders can hone their incident response skills, assess the effectiveness of security controls, and identify areas for improvement in their cyber defence strategies. Cyber Range platforms offer a safe space for hands-on learning, allowing security professionals to experience the pressure and complexity of cyber incidents without risking real-world consequences.
Conclusion:
In conclusion, the realm of cybersecurity is currently experiencing an era of unparalleled advancements propelled by rapid technological innovation and the continuously evolving landscape of digital threats. This dynamic environment necessitates a multifaceted approach to defence, leveraging a variety of sophisticated tools and techniques to fortify digital infrastructures.
One of the most prominent developments in cybersecurity is the integration of artificial intelligence (AI) and machine learning (ML) algorithms. These technologies enable organizations to analyse vast amounts of data in real time, identifying patterns and anomalies indicative of potential security breaches with greater accuracy and speed than ever before. By leveraging AI and ML, organizations can enhance their threat detection capabilities and respond to cyber threats more effectively.